使用Frida + DroidSSLUnpinning后App自动重启,仍然无法抓包
模拟器已开启Frida-server服务,输入命令:frida -U -f com.goldze.mvvmhabit -l hooks.js --no-pause后App提示停止运行,重启后仍然提示证书验证失败,使用逍遥模拟器安卓7版本,frida使用最新版本15.2.2
(base) C:\Users\29571\Desktop\workspace\python\python3WebSpider\Chapter 13 Android逆向\Droidsslunpinning\ObjectionUnpinningPlus>frida -U -f com.goldze.mvvmhabit -l hooks.js --no-pause
____
/ _ | Frida 15.2.2 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://frida.re/docs/home/
. . . .
. . . . Connected to VOG AL00 (id=127.0.0.1:21503)
Spawned `com.goldze.mvvmhabit`. Resuming main thread!
[VOG AL00::com.goldze.mvvmhabit ]-> message: {'type': 'send', 'payload': 'Custom, Empty TrustManager ready'} data: None
message: {'type': 'send', 'payload': 'OkHTTP 3.x Found'} data: None
message: {'type': 'send', 'payload': 'com.squareup.okhttp not found'} data: None
message: {'type': 'send', 'payload': 'registerClass from hostnameVerifier >>>>>>>> Missing implementation for: boolean verify(java.lang.String, javax.net.ssl.SSLSession)'} data: None
message: {'type': 'send', 'payload': 'Xutils hooks not Found'} data: None
message: {'type': 'send', 'payload': 'httpclientandroidlib Hooks not found'} data: None
message: {'type': 'send', 'payload': 'OpenSSLSocketImpl pinning'} data: None
[-] Cronet pinner not found
message: {'type': 'send', 'payload': 'Trustkit pinner not found'} data: None
Process crashed: Bad access due to invalid address
***
*** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
Build fingerprint: '22.355.07.00.00/22.355.07.00.00/22.355.07.00.00:7.1.2/20171130.376229:user/release-keys'
Revision: '0'
ABI: 'x86_64'
pid: 3395, tid: 3395, name: flush-8:0 >>> 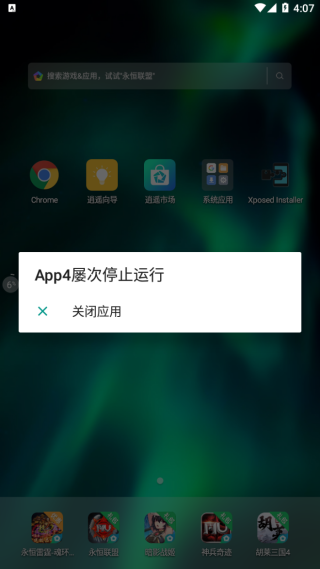
重新建了一个模拟器,配置好Frida后,可以成功抓包了,不知道是不是之前那个模拟器装了xposed导致某种Bug